The New Mandate for the CISO

From Technical Guardian to Business Strategist
The role of the Chief Information Security Officer (CISO) has undergone a seismic shift. A decade ago, the CISO was a technical guardian, a firewall-and-endpoints guru deep within the IT organization. Today, that CISO is gone. In their place is a boardroom-level business strategist, an owner of enterprise risk, and the focal point of intense legal and regulatory scrutiny.
It’s no longer about deploying security tools; it's about delivering executive results. The board doesn't want to hear about malware signatures; they want to know how you are safeguarding shareholder value and maintaining customer trust. Two powerful drivers are forcing this new mandate.
First, the financial stakes have mushroomed. According to IBM's 2024 Cost of a Data Breach Report, the average cost has ballooned to $4.88 million. This staggering figure isn't just recovery cost; it encompasses regulatory fines, customer churn, brand damage, and business downtime. A single breach can erase a year's profitability, making cybersecurity a Tier 1 topic in corporate governance.
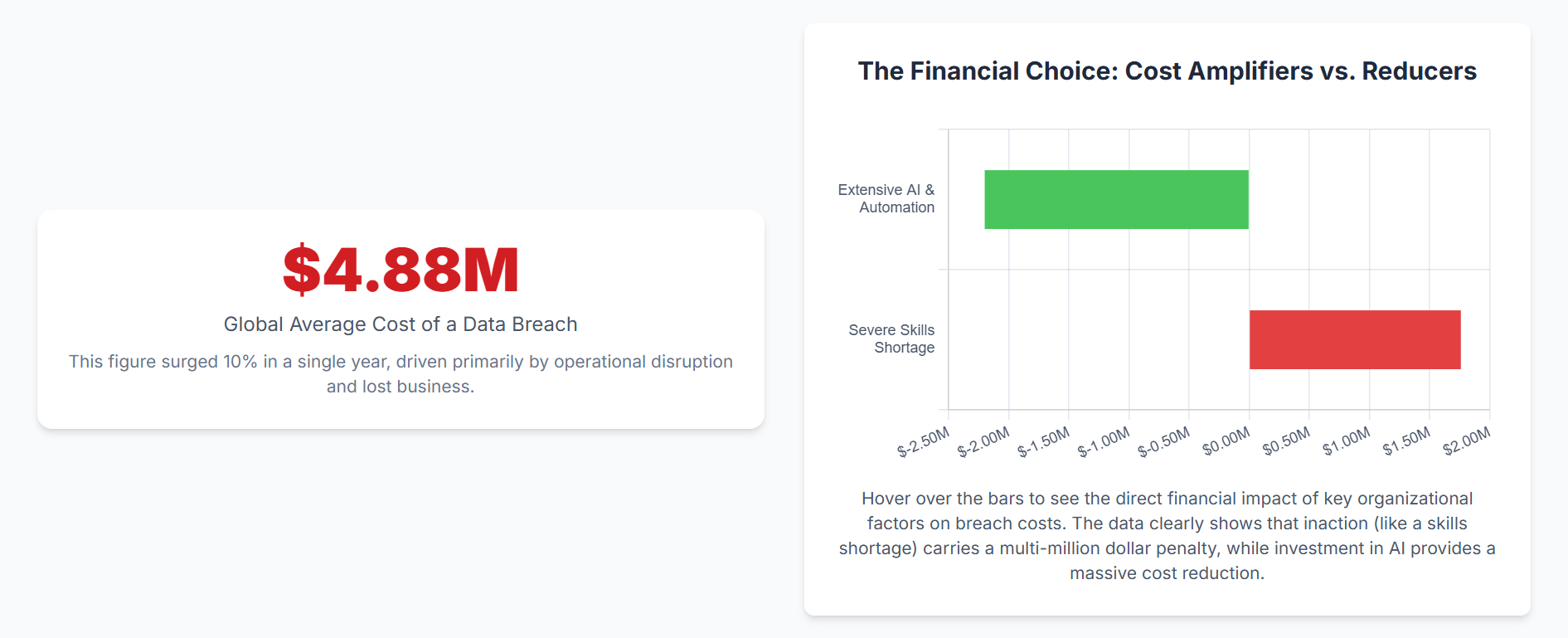
Second, the era of personal liability has arrived. Courts and regulators are shattering the assumption that liability ends at the company door. The conviction of Uber's former CSO for obstruction of justice and the SEC's fraud charges against SolarWinds' CISO established a chilling precedent. Negligence, misrepresentation, or a failure to demonstrate due diligence can now lead to personal liability, endangering your career, reputation, and financial security.
This article explores why the traditional, human-scale Security Operations Center (SOC) is an indefensible liability in this high-stakes environment. More importantly, it charts the necessary evolution toward an AI-driven, agentic security model—the most effective way to mitigate both corporate and personal risk.
The Breaking Point: Why the Human-Scale Security Operations Is No Longer Defensible
The core problem of the modern SOC is not a dearth of energy or talent; it is one of inherent incompatibility of scale and tempo. Your teams are waging an asymmetric war. They are human artisans, slowly analyzing each threat individually, as attackers are deploying mechanized, industrial-strength assault factories. Asymmetry manifests in a series of catastrophic points of failure that every CISO can attest to all too well.
The Data Deluge and Tool Sprawl
The modern-day business operates under the advanced ecosystem of technology, and we have implemented an equally advanced ecosystem of security measures to protect it. Endpoint detection and response (EDR), Security Information and Event Management (SIEM), cloud security posture management (CSPM), identity providers—and the list continues. They are all sources of good information individually, but as a group, they form an ocean of data.
This "sprawl of tools" has had a direct impact: a deluge of data. Your average SOC analyst may be tasked with monitoring dozens of distinct dashboards and consoles, showing thousands of alerts across the span of a single shift. That "single pane of glass" promise has rarely materialized. Your staff is instead reduced to manually stitching together context from a quiltwork of systems, a clumsy process that invites error.
The Choking Weight of Alert Fatigue
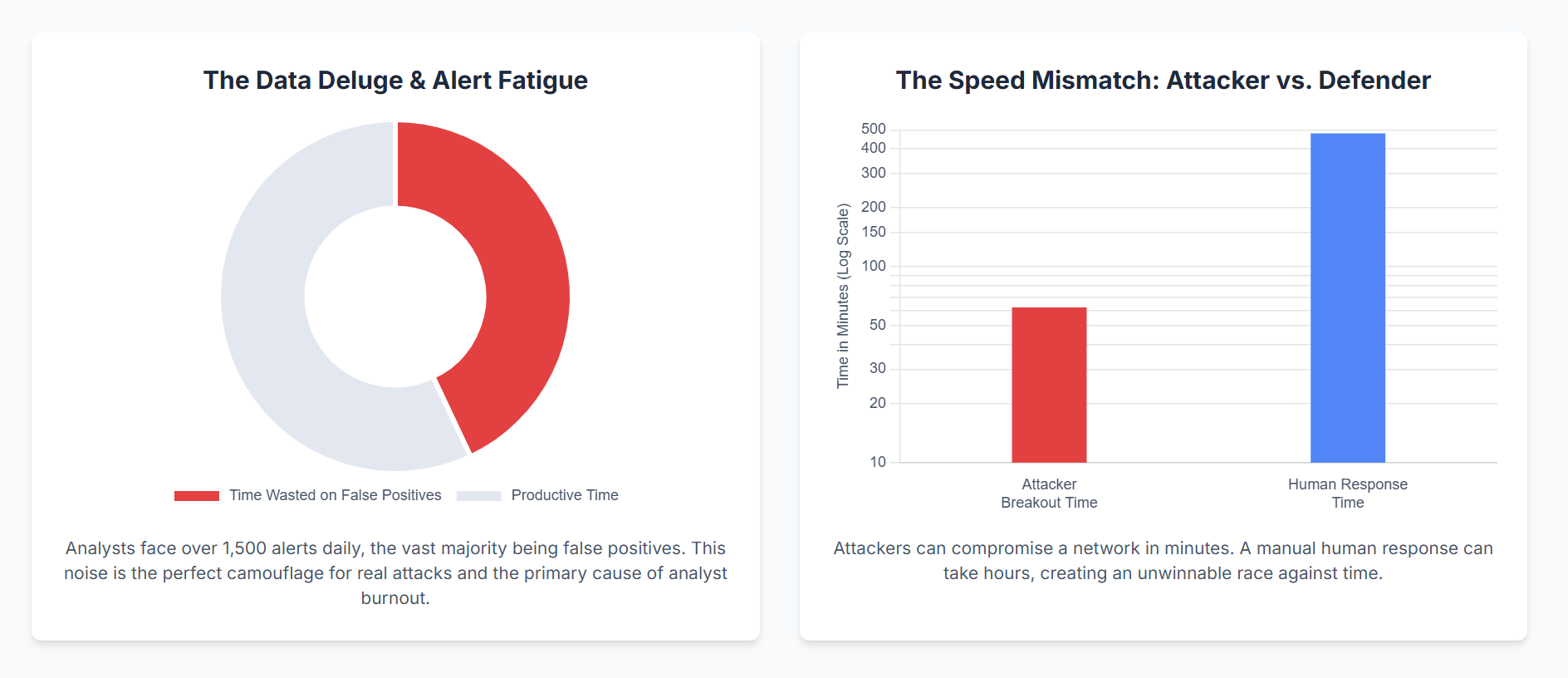
With everything being an alert, then nothing is an alert. The choking reality for most SOCs is that the vast majority of the alerts they investigate—often more than 80%—prove to be false positives. All the noise has two deeply dangerous impacts:
Analyst Burnout and Attrition:
Cybersecurity skills gap is among the largest threats in the industry. They don't have sufficient qualified professionals to fill the openings, and the ones you do have are being maxed out. Alert fatigue is one of the largest contributors to burnout, which leads to turnover and loss of valuable institutional memory. The hiring cost and training cost is enormous, and the cycle repeats itself.
Camouflage of Real Attacks:
A noisy environment is the perfect disguise for an actual attack. Advanced attackers know that SOCs are overwhelmed. They can deliberately make low-and-slow noise in the background to mask their true activity, knowing that the one critical alert pointing to their presence will be drowned out by an ocean of tens of thousands of harmless notifications. The majority of the most devastating all-time breaches were caused not by a previously unknown vulnerability, but by an ignored warning.
The Unrecoverable Race Against Time
Automated attack tools can compromise credentials and move laterally across a network in minutes. A recent Mandiant study found the median attacker "breakout time"—the time from initial compromise to lateral movement—is a mere 62 minutes.
Compare that to a typical manual investigation:
- An alert appears in a queue.
- Hours later, an analyst picks it up.
- The analyst manually pivots between tools to gather context: user identity, endpoint data, process history, IP reputation.
- The analyst attempts to correlate these disparate data points.
- If deemed plausible, the threat is escalated to a senior analyst, and the cycle repeats.
This sequential, human-gated process can take hours, if not days. By the time your team confirms a threat is real, the attacker has already achieved their objective. You are competing in a race you were designed to lose.
The Solution: Augmenting Humans with Agentic AI
To solve a machine-scale problem, you need a machine-scale solution. But this is not about replacing your personnel; it's about actually changing the job they do. The idea is to elevate your experienced human analysts out of reactive alert investigators to proactive threat hunters and incident commanders. This is achieved by introducing a new player: the AI SOC Analyst.
At Arambh Labs, we are pioneering this new agentic security model. We build AI agents as independent teammates who work in concert with your human experts to examine every alert, machine speed, with flawless consistency.

By automating the initial investigation of all original alerts, an AI SOC removes the attacker's speed advantage. It has a consistent, auditable record of every action taken—a necessary element in establishing due diligence and protection against claims of negligence. The mundane, repetitive work is done by the AI entity, freeing your human resources to apply creativity, intuition, and strategic thinking to the most complex challenges.
Your New Strategic Imperative
As a CISO, your power is no longer technical anymore; it's strategic. You're being entrusted with supervision over a significant financial exposure to the company and a direct personal exposure to you.
To keep relying on a human-centric SOC model in the face of machine-paced assaults is akin to sending musket-wielding soldiers up against an enemy that employs drones. The outcome is already a given.
Adopting an AI-driven, agentic approach is the most logical and efficient step to protect your organization and your own career. It transmutes your SOC from a reactive expense center, perpetually stuck trying to keep up, into a proactive, strategic resource with the potential to demonstrate real business value. It allows you to have faith in addressing the board's questions about risk, resiliency, and return on investment, backed by an operational model crafted for the realities of modern cyber warfare.
Frequently Asked Questions (FAQ)
- Will AI replace my human SOC team?
No. This is likely one of the most common myths. Agentic AI is not about replacement, but about augmentation. It is intended to eliminate the mundane, tedious, and soul-destroying parts of a security analyst's job—the parts that lead to burnout. By streamlining the examination of every alert, AI frees your skilled human analysts to focus on activities of greater value like proactive hunting, reverse engineering malware samples, developing new detection techniques, and resolving complicated incidents. Your analysts are more productive, more engaged, and more strategic. - How can I trust an AI's decision?
Trust depends on transparency and control. A properly designed AI SOC analyst is not a "black box." Every action it takes, all the information it asks about, and all of its findings are diligently logged in human-readable format. This yields a wonderful, unalterable audit trail for every inquiry. Also, the system is human-in-the-loop enabled for auditability. You control the rules of engagement and the points at which a human expert must validate an action, so you always have ultimate control. - What does an "Agentic security platform" do differently than the "AI" in my existing SIEM?
This is a good distinction. Much of the "AI" functionality in outdated security products is passive machine learning algorithms. They do great at pattern matching—finding anomalies or correlating similar events. But they are not autonomous. They still require an individual to look at the output, interpret it, and then start a human inquiry. An agentic AI SOC analyst is quite a different proposition. It is an engaged independent entity. It does not just report information; it acts. It independently poses questions to systems, enhances information, cross-correlates results, and makes conclusions, effectively performing the role of a human analyst for the initial 99% of the investigation. - In what ways does this approach help with compliance and documentation of due diligence?
In the current regulatory climate, being able to demonstrate a consistent, repeatable, and auditable security process is essential for limiting liability. Our agentic ai platform provides this by design. Every alert, no matter how minor, is investigated and documented with perfect consistency, 24/7. This creates an unimpeachable record of due diligence that is simply impossible to achieve with a purely manual process, which is subject to human variability, fatigue, and error. - What does "agentic" security entail?
"Agentic" is the characteristic that an AI system can act by itself in order to achieve a goal. In this case, an AI agent is defined with the goal of "investigate and determine the nature of this alert." It can subsequently decide itself what actions to execute—ask an EDR, query threat intelligence feeds, inspect user activity—to achieve that goal. It is the difference between a calculator (a device that needs human input for every step) and an autonomous vehicle (an agent that can drive through a complicated environment on its own without human assistance). Agentic security is the future of the SOC.